Freenet Routing
This page describes how to run freenet as a user on your machine and
route all the traffic from that user (here the username is
fn) via a specific network interface.
My Setup
First lets see my setup and specific configuration, you can easily change this to your requirements.

Here you can see that my OpenVPN server, configured to use persistent IP addresses, is hosted in a datacentre somewhere (bottom left). I have two clients which are constantly connected to the OpenVPN server, the Raspberry Pi and Riker (both of which run freenet).
I am happy with the Raspberry Pi running and using the home connection but I want Riker to route all the Freenet traffic through the VPS but all other traffic should be handled normally.
Setup OpenVPN on your VPS
I will assume you know how to do this, if not there is lots of documentation on how to do it on the OpenVPN website. Below is my server configuration:
dev tun proto tcp port 1194 ping 60 ping-restart 300 ping-timer-rem push "ping 60" push "ping-restart 300" ca /etc/openvpn/easy-rsa/keys/ca.crt cert /etc/openvpn/easy-rsa/keys/server.crt key /etc/openvpn/easy-rsa/keys/server.key dh /etc/openvpn/easy-rsa/keys/dh2048.pem server 192.168.51.0 255.255.255.0 ifconfig-pool-persist /etc/openvpn/ipp.txt persist-key persist-tun status /var/log/openvpn-1194-status.log verb 3 client-to-client log-append /var/log/openvpn-1194 comp-lzo
Setup MASQUERADING on the VPS
This is quite easy but many people have their own way of doing it, security and whatnot but I will just setup a basic NAT for all IP addresses on my OpenVPN network:
iptables -t nat -A POSTROUTING --src 192.168.51.0/24 -o eth0 -j MASQUERADE echo 1 > /proc/sys/net/ipv4/ip_forward echo 0 > /proc/sys/net/ipv4/conf/all/rp_filter
Naturally, these are not going to persist across reboots, if you
want this please investigate /etc/sysctl.conf. Also,
you may not need to disable the reverse path filter
(rp_filter) I did but your mileage my vary.
Setting up the Client (Riker)
Again, I am assuming you have configured and have OpenVPN running on the client machine.
Firstly you must have the ability to mark packets based on owner, in menuconfig you will find it in:
Networking Support ->
Networking Options ->
Network Packet Filtering Framework (Netfilter) ->
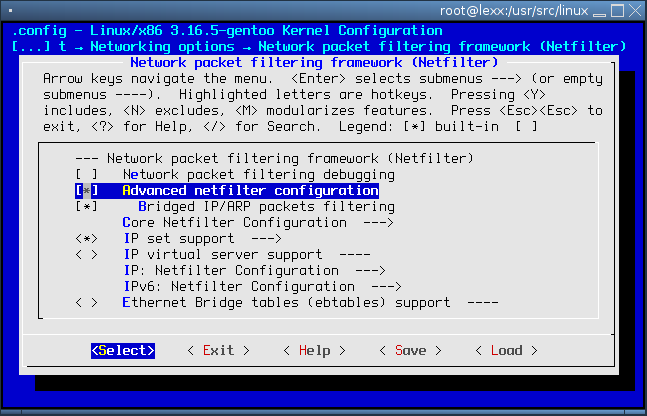
In Core Netfilter Configuration --> select "owner"
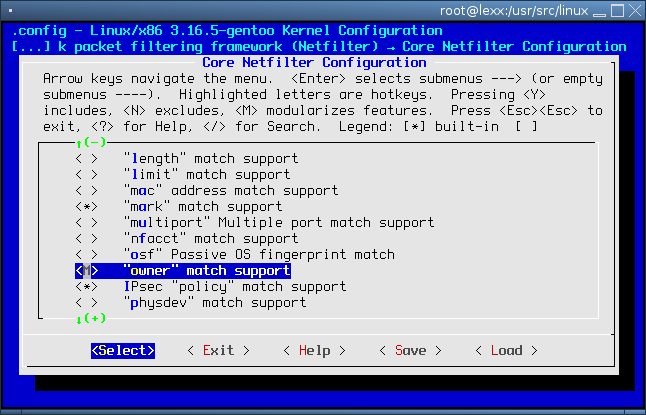
If you are not confident with kernel recompilation, don't worry your distro may already have included this as a module.
Adding the Routing Table
OpenVPN or whatever must be running at this point, or this will not work, please make sure it is.
We are going to create a special routing table for the
fn user, this will route all their traffic over the VPN
interface (in my case tun0.
Open /etc/iproute2/rt_tables with your favourite editor,
mine looks like this:
#
# reserved values
#
255 local
254 main
253 default
0 unspec
#
# local
#
126 fntraf
My modification is in red, save and close the file. You should
now have another routing table which you can configure with the
ip route command.
ip route add 192.168.51.33 dev tun0 table fntraf ip route add default via 192.168.51.33 dev tun0 table fntraf
You should now be able to see the table by typing in ip
route show table fntraf. This is all fine but nobody is using
this routing table so what use is it? We need some way of
identifying packets which are to be sent through this routing table, to
do this we are going to use iptables marking.
First, mark the packets. One thing to note here is that marking ONLY
works in the mangle table... it can be put in others but it
will not do anything! Took me a while to find this.
iptables -t mangle -A OUTPUT -m owner --uid-owner fn -j MARK --set-mark 0xa
Now we have marked all the packets for that user, groups
and stuff like that works too. Now that the packets are marked we
must set up a rule to push the packets down our fntraf
table rather than the default ones.
ip rule add from all fwmark 0xa lookup fntraf prio 126 ip route flush cache
Yippee!! if you try tcpdump -i tun0 you should see
packets sent on the interface... you may notice something rather odd
though, the source IP Address is not what you might expect. We will
re-write it with SNAT:
iptables -t nat -A POSTROUTING -o tun0 -j SNAT --to 192.168.51.34
Now you will probably find (using netcat and UDP) that you can send
packets one way (from your client to an internet server but responses
will get dropped... odd since you should also be able to see the
responses in tcpdump!! One last step is to disable the
reverse path filter on your client machine:
echo 0 > /proc/sys/net/ipv4/conf/tun0/rp_filter echo 0 > /proc/sys/net/ipv4/conf/all/rp_filter
As you have disabled the reverse path router it might be an idea to set up some firewall rules to make up for it. I leave this as an exercise for you my dear reader. Also, none of these changes are persistent and so you will have to put them in a script or something!
I hope this was helpful, I realise this is a special case but who knows it may be helpful to someone out there!
References
- http://unix.stackexchange.com/questions/21093/output-traffic-on-different-interfaces-based-on-destination-port
- http://www.cyberciti.biz/tips/block-outgoing-network-access-for-a-single-user-from-my-server-using-iptables.html
- http://www.linuxquestions.org/questions/linux-networking-3/iptables-marking-ip-rule-add-fwmark-1-table-200-ip-route-add-via-gw-table-200-a-500369/
- http://lkml.iu.edu/hypermail/linux/net/1001.2/00005.html

